Notes Juniper EX
Summary
JunOS – OS pour toute les gammes Juniper
=>T640/M120/M10/71/EX Series
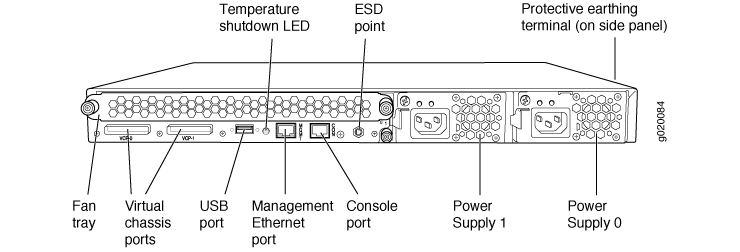
EX series switches:
type-slot/pic/port
• type—:
o ge— interface Ethernet Gigabit
o xe— interface 10 Gigabit Ethernet
• slot number/member-id— de 0 à 9 – 0 pour un switch unique, et plus pour les virtual-chassis.
• PIC—0 pour la partie de gauche, et 1 pour les Uplinks.
• port—Le port, de 0 à 47, correspond au port physique sur le switch.
- Control plane (Routing/switching tables)
- -> CPU/memoire indépendante du forwarding place
- Forwarding Plane (Forwarding tables)
- -> Asics..etc.
Managing JunOS
CLI => Consoole/telnet/SSH
GUI => J-Web
Junos Swript API
Netconf
NetScrenn Security manager
CLI fundamentals
Operational mode (exec):
user@host> benoit@switch>
Configuration mode (conf t):
user@host>configure [edit] user@host# benoit@switch#
Auto-complétion: [espace]
Pipes:
show interfaces terse | last show interfaces terse | count show interfaces terse | match <pattern> show interfaces terse | except show interfaces terse | find show interfaces terse | last |match
CONFIGURATION Fundamentals
Meilleur sense hiérarchique par rapport à l’IOS.
Configuration découpée en sections
Multiples niveaux de hierarchies
Niveaux identifiées avec les {}
hostname / password:
system {
host-name s4;
root-authentication {
encrypted-password "ertyu65432zearztgyhu7654REftg"; ##SECRET-DATA
}
}
configuration avec 2 commandes set.
Top-level configuration Elements:
- system – paramètres généraux (hostname, authentification, méthodes d’acces, logging..)
- interfaces
- protocols – L2/L3 protocols
- policy-options – règles de routage
- firewall – filtrage de paquet stateless
- snmp
- class-of-service
- poe
- virtual-chassis
- vlans
- ethernet-switching-options
Candidate configuration
IOS : running-config
JunOS : running-config + candidate config
Candidate vs. Active:
Candidate = copy de la configuration active + edits + edits ..etc.
Après un commit, elle passe en Active/running.
JunOS garde en mémoire les 50 dernière versions commitées.
On peut charger une des 50 versions en “candidate”
configure => plusieurs utilisateurs peuvent modifier en meme temps
configure exclusive => on est le seul à effectuer des modifs
configure private => chacun sa configuration privée, pour ne pas créer de conflits, sinon le CLI l’informe pendant le commit
Making changes:
root@s4>configure
[edit]
root@s4#edit interfaces ge-0/0/9
[edit interfaces ge-0/0/9]
root@s4#edit unit 0
[edit interfaces ge-0/0/9 uni 0]
root@s4#set family inet address 172.20.1.1/24
[edit interfaces ge-0/0/9 uni 0]
root@s4#show
family inet {
address 172.20.1.1/24;
}
[edit interfaces ge-0/0/9 uni 0]
root@s4#delete family inet address 172.20.1.1/24
[edit interfaces ge-0/0/9 uni 0]
root@s4#show
family inet;
[edit interfaces ge-0/0/9 uni 0]
root@s4# delete family inet
[edit interfaces ge-0/0/9 uni 0]
root@s4# show
[edit interfaces ge-0/0/9 uni 0]
root@s4# up
[edit interfaces ge-0/0/9]
root@s4# top
[edit]
root@s4# show interfaces
ge-0/0/9 {
unit 0;
}
Running operationnal-mode in config-mode
pour faire des ping, ou des show interfaces en mode de configuration:
root@s4#run show interfaces root@s4#run ping 10.210.1.2
Préparer les changements:
on peux configurer des interfaces qui ne sont encores pas présentes physiquement.
mais on les désactive.
Ex:
root@s4#edit protocoles dot1x
[edit protocoles dot1x]
root@s4#set authenticator interface ge-0/0/3.0
[edit protocoles dot1x]
root@s4#deactivate authenticator interface ge-0/0/3.0
[edit protocoles dot1x]
root@s4#show
authenticator {
interface {
inactive: ge-0/0/3.0;
ge-0/0/4.0;
}
}
[edit protocoles dot1x]
root@s4#commit
commit complete
[edit protocoles dot1x]
root@s4# run show dot1x interface brief
802.1x information
Interface Role State
ge-0/0/3.0 None
ge-0/0/4.0 Authenticator Initialize
[edit protocoles dot1x]
root@s4#activate authenticator interface ge-0/0/3.0
[edit protocoles dot1x]
root@s4#commit
commit complete
[edit protocoles dot1x]
root@s4#run show dot1x interface brief
[edit protocoles dot1x]
root@s4# run show dot1x interface brief
802.1x information
Interface Role State
ge-0/0/3.0 Authenticator Connecting
ge-0/0/4.0 Authenticator Initialize
On peut aussi désactiver des sections entières.
root@s4#deactivate dot1x
root@s4#deactivate protocols
[…]
Bouger une configuration de ge-0/0/5 à ge-0/0/6:
root@s4#rename interfaces ge-0/0/5 to ge-0/0/6
root@s4#commit
Rename vs. replace
rename: renommer un unique element
replace: changer les références d’une interface a une autre
Ip addresses:
on peux attribuer plusieurs ip à une interfaces.
set unit 0 family inet address 172.20.11.1/24 primary
set unit 0 family inet address 172.20.12.1/24
set unit 0 family inet address 172.20.13.1/24
Accepter les changements (commit)
commit check
commit at “2012-12-23 00:01”
commit confirmed 1
commit and-quit
Annuler les changements (rollback)
rollback => charge la config active en candidate.
show | compare rollback “number”
show compare (diffrence entre candidate/active)
M/T series: fe-2/1/0
type-fpc/pic/port
Ex series: ge-0/1/2
type-VCnumber/module/port
ge : Gigabit
xe : 10-gig
interfaces spéciales:
lo0 – loopback
me0 – Out-of-band Ethernet
vme – Virtual management Ethernet (virtual-chassis)
vlan – VLAN interface (L3)
Units:
IOS: subinterfaces
JunOS : Units
L2
ge-0/0/4 {
L2 // ether-options {
L2 // no-auto-negocation;
L2 // link-mode full-duplex;
L2 // speed {
L2 // 100m
L2 // }
L2 // }
L3 // unit 0 {
L3 // family ethernet-switching;
L3 // }
}
VLAN
interfaces {
vlan {
unit 2 {
description Printers;
family inet {
address 192.168.2.2/24;
}
}
unit 3 {
description Phones;
family inet {
address 192.168.3.2/24;
}
}
unit 100 {
description Example;
family inet {
address 192.168.100.2/24;
}
}
}
}
L2 = ethernet-switching
– port-mode (access/trunk)
– VLANs
– Stateless packet filters
L3 = inet
Exemple:
set unit 0 family ethernet-switching
set unit 0 family inet
Activer les interfaces:
IOS: shutdown/no shutdown
JunOS: deactivate : ignorée par JunOS
disable : shutdown
SWITCHING CONFIGURATION
EX Series switches : 10/100/1000 Ethernet ports.
Par défaut, ils sont en auto-négo.
run show interfaces ge-0/0/3 extensive | find Autoneg
Autonegociation information:
Negociation status: Complete
Link partner:
Link mode: Full-duplex, flow control: None, ..
ink partner speed: 100 Mbps, Reason: Link paartner failure
Local resolution;
Flow control: None, Remote fault; Link OK
root@s4#edit interface ge-0/0/4 ether-options
root@s4#set speed 100m
root@s4#set link-mode full-duplex
root@s4#commit
Désactiver l’auto-nego:
set interfaces ge-0/0/4 ether-options no-auto-negociation
Aggregated Ethernet
IEE 802.3ad supporté.
– Créer un aggrégat
– Associer les ports dans cet aggrégat
– Configurer l’aggrégat
root@s4#edit chassis aggregated-devices
root@s4#set ethernet device-count 1
root@s4#show
ethernet {
device-count 1;
}
root@s4#set interfaces ge-0/0/5 ether-options 802.3ad ae0
root@s4#set interfaces ge-0/0/6 ether-options 802.3ad ae0
root@s4#show
ge-0/0/5 {
ether-options {
802.3ad ae0;
}
}
ge-0/0/6 {
ether-options {
802.3ad ae0;
}
}
root@s4#edit interfaces ae0
root@s4#set unit 0 family ethernet-switching port-mode trunk
root@s4#set aggregated-ether-options lap active
root@s4#commit
root@s4#show
aggregated-ether-options {
lacp {
active;
}
}
unit 0 {
family ethernet-switching {
port-mode trunk;
}
}
Proxy ARP
Quand un hote demande une mac au switch, alors que l’IP n’est pas sur le meme VLAN, le switch peux faire proxy, et donner sa MAC.
root@s4#edit interfaces ge-0/0/7unit 0
root@s4#set proxy-arp
root@s4#show
proxy-arp;
family inet {
address 192.168.207.1/24
}
VLANs
root@s4#edit vlans
root@s4#set example
root@s4#set example vlan-id 100
root@s4#show
Name Tag Interfaces
example 100 None
phones 3 ae0.0*
printers 2 ae0.0*
Access-ports
root@s4#set example interfaces ge-0/0/7.0
root@s4#top edit interfaces
root@s4#set ge-0/0/7 unit 0 family ethernet-switching
root@s4#set ge-0/0/8 unit 0 family ethernet-switching vlan members 100
root@s4#set ge-0/0/9 unit 0 family ethernet-switching vlan members example
root@s4#up
root@s4#commit
root@s4#show vlan example
vlan-id 100;
interfaces {
ge-0/0/7.0;
ge-0/0/8.0;
ge-0/0/9.0;
}
Trunk-ports
root@s4#set vlans phones interfaces ge-0/0/7.0
root@s4#set vlans printers interfaces ge-0/0/7.0
root@s4#commit check
Access interface error…
root@s4#set ge-0/0/7 unit 0 family ethernet-switching port-mode trunk
root@s4#commit check
configuration check succeeds
root@s4#set ge-0/0/8 unit 0 family ethernet-switching port-mode trunk
root@s4#set ge-0/0/8 unit 0 family ethernet-switching vlan members [ 2 3 ]
root@s4#set ge-0/0/8 unit 0 family ethernet-switching port-mode trunk
root@s4#set ge-0/0/8 unit 0 family ethernet-switching vlan members [ phones printers ]
root@s4#commit
root@s4#set ge-0/0/9 unit 0 family ethernet-switching native-vlan-id default
root@s4#show
unit 0 {
family ethernet-switching {
port-mode trunk;
vlan {
members [ example phones printers ];
}
native-vlan-id default;
}
}
root@s4#commit
Routed VLAN interface
root@s4#edit vlans
!Assignation d’une interface de couche3 au VLAN “example”
root@s4#set example 13-interface vlan.100
root@s4#top edit interfaces vlan
root@s4#set unit 100 description example
root@s4#set unit 100 family inet address 192.168.100.2/24
root@s4#commit
show interfaces descriptions show interfaces terse
interfaces
show interfaces ge-0/0/7 show interfaces ge-0/0/7 brief show interfaces ge-0/0/7 detail show interfaces ge-0/0/7 extensive
Switchport
show interfaces switchport show interfaces trunk show ethernet-switching interfaces
VLANS
show vlans show vlans id brief show vlans id detail show vlans id extensive
MAC
show ethernet-switching table show ethernet-switching mac-learning-log
SECURITY
Filtrage de paquets stateless, comme les ACL Cisco.
First term => match => action
Second term => match => action
Discard/drop
Ex IOS:
access-list 100 deny ip 192.168.0.0 0.0.0.255 any access-list 100 permit ip any any
Ex JunOS (the same):
[edit firewall family inet]
root@s4#show
filter sample-filter {
term block-bad-subnet {
from {
source-address {
192.168.0.0/24;
}
}
then {
discard;
}
}
term accept-all {
then accept;
}
}
root@s4#edit filter sampl-filter term block-bad-subnet from source-address root@s4#annotate 192.168.0.0/24 "requested by john doe" root@s4#annotate 192.168.10.0/24 "requested by Ben"
JunOS utilise le masque standard (CIDR), pas de wildcard.
performance
Filtres de firewall compilés.
matching optimisé..
pas besoin normalement d’optimiser les filtres.
Avec la méthode de configuration active/candidate, le firewall est toujours en marche.
Pas comme sur cisco quand on doit supprimer et recréer certaines ACL (sauf pour celles avec numéro de sequence..:)).
Appliquer les filtres du firewall
root@s4#set interfaces vlan.2 family inet filter input sample-filter
Other security features
802.1x authentication
limite de MAC
DHCP inspection
Firewall/802.1X pour assigner de la CoS
Exercise:
root@s4#show firewall
root@s4#edit firewall family ethernet-switching filter my-vlan-filter
root@s4#edit term block-bad-mac
root@s4#set from source-mac-address 00ca.1234.1121
root@s4#set then discard
root@s4#up 1
root@s4#edit term allow-ping
root@s4#set from protocol icmp
root@s4#set from icmp-type echo-request
root@s4#set from icmp-type echo-reply
root@s4#set then accept
root@s4#up 1
root@s4#edit term block-icmp
root@s4#set from protocol icmp
root@s4#set then discard
root@s4#set term default-accept
[edit firewall family ethernet-switching filter my-vlan-filter]
root@s4#show
term block-bad-mac {
from {
source-mac-address {
00:ca:12:34:11:21;
}
}
then discard;
}
term allow-ping {
from {
protocol icmp;
icmp-type [ echo-request echo-reply ];
}
then accept;
}
[...]
root@s4#top
root@s4#set vlans accounting filter input my-vlan-filter
SPANNING-TREE
STP / RSTP /MSTP… bla bla.. ok.
Configuration STP:
root@s4#set protocols stp root@s4#show protocols stp; root@s4#set protocols stp bridge-priority 20k root@s4#set protocols stp interface ge-0/0/1 disable root@s4#set protocols stp interface ge-0/0/2 cost 1000 root@s4#set protocols stp interface ge-0/0/9 edge // portfast
Configuration RSTP:
root@s4#show protocols stp | display set
set protocols stp bridge-priority 20k
set protocols stp interface ge-0/0/1.0 disable
set protocols stp interface ge-0/0/2.0 cost 1000
set protocols stp interface ge-0/0/9.0 edge // portfast
root@s4#delete protocol stp
root@s4#set protocols rstp bridge-priority 20k
root@s4#set protocols rstp interface ge-0/0/5.0 disable
root@s4#set protocols rstp interface ge-0/0/6.0 cost 1000
root@s4#set protocols rstp interface ge-0/0/9.0 edge
root@s4#
root@s4#set protocols rstp interface ge-0/0/6.0 mode point-to-point
root@s4#show protocols
rstp {
bridge-priority 20k;
interface ge-0/0/5.0 {
disable;
}
interface ge-0/0/6.0 {
cost 1000;
mode point-to-point;
}
[...]
}
Configuration MSTP:
root@s4#delete protocols Rstp root@s4#set protocols mstp bridge-priority 20k root@s4#set protocols mstp interface ge-0/0/1 disable root@s4#set protocols mstp interface ge-0/0/2 cost 1000 root@s4#set protocols mstp interface ge-0/0/9 edge root@s4#set protocols mstp interface ge-0/0/9 mode point-to-point root@s4# root@s4#set protocols mstp configuration-name example root@s4#set protocols mstp msti 1 vlan [ 1 3 5 ] root@s4#set protocols mstp msti 2 vlan [ 2 4 6 ] root@s4#
Vérifications:
show spanning-tree bridge show spanning-tree interface show ethernet-switching interfaces
INTRODUCTION TO ROUTING
Overview:
IOS JunOS
— —–
show ip route show route
show ip bgp sum show bgp sum
show ip bgp nei show bgp nei
show ip ospf show ospf
Tables de routage
root@s4>show route inet.0: 18 destinations, 25 routes (18 actives, 0 holddown, 1 hidden) + = Active Route, - = Last Active, * = Both 0.0.0.0/0 *[OSPF/150] 5d 19:40:04, metric 1, tag 0 > to 10.10.245.234 via vlan.20 10.14.240.0/22 *[Aggregate/130] 1w1d ... [...]
Route preferences:
| Source | Default Preference |
| Direct | 0 |
| Local | 0 |
| Static | 5 |
| OSPF Internal | 10 |
| RIP | 100 |
| Aggregate | 130 |
| OSPF AS External | 150 |
| BGP | 170 |
Troubleshooting:
root@s4>show route hidden root@s4>show route hidden extensive root@s4>show route x.x.x.x/x root@s4>show route root@s4>show route x.x.x.x/x exact root@s4>show route x.x.x.x/x exact extensive
Static routes :
root@s4>set static route x.x.x.x/x next-hop x.x.x.x root@s4>set static route default next-hop x.x.x.x root@s4>set qualified-next-hop x.x.x.x interface vlan.3 root@s4>set qualified-next-hop x.x.x.x preference 30
OSPF
Configuration:
root@s4# set area 2 interface vlan.5
root@s4# set arrea 2 interface ge-0/0/4.0
root@s4# set arrea 2 interface ge-0/0/4.0 passive
root@s4# set arrea 2 interface vlan.5 metric 200
[edit protocols ospf]
root@s4#show
area 0.0.0.2 {
interface vlan.5 {
mteric 200;
}
interface ge-0/0/4.0 {
passive;
}
}
root@s4#
root@s4#
Area types:
[edit protocols ospf]
root@s4#set area 2 stub
root@s4#set area 3 nssa
root@s4#set area 3 interface vlan.6
root@s4#set area 2 stub default
root@s4#set area 3 nssa default-lsa default-metric 1
root@s4#show
area 0.0.0.2 {
stub default-metric 1;
interface vlan.5 {
mteric 200;
}
interface ge-0/0/4.0 {
passive;
}
}
area 0.0.0.3 {
nssa {
default-lsa default-metric 1;
}
interface vlan.6;
}
Injecter des routes dans OSPF:
il faut utiliser une “export policy”
pas plus de détail dans ce cours.
Authentification:
[edit protocols ospf area 0.0.0.2] root@s4#set interface vlan.5 authentication md5 1 key test
Vérification:
show ospf database show ospf interface
show ospf interface vlan.2 extensive
show ospf neighbor
show route protocol ospf
3 Comments
Comments are Disabled



[…] This post was Twitted by BenoitGONCALVES […]
je peux avoir la configuration basic de juniper srx 100 par ligne de commannde
la creation de vlan sur un juniper EX-4200P en ligne de commande